It's amazing how many people are interested in learning how to hack something in kali linux Could it be because they usually have a Hollywood like Mr. Robot impression on their minds?
However, we must to say thanks to the open source community, because of them, we can list 20 tools for hacking in kali linux to meet all your needs. Just remember to keep it ethical! and educational purpose only.
Most people are interested in pentesting and hacking because like magic from nothing becomes there. and how to manipulate data provided by computers and technology.
HERE IS THE BEST :
20 TOOLS FOR HACKING IN KALI LINUX
1. Metasploit Framework
Metasploit Framework is an open source framework where experts and security teams check security vulnerabilities and perform security assessments to improve security knowledge.
 |
| Credit : WikiMedia |
It contains a large number of tools through which you can create security environments to test vulnerability and act as a penetration test system.
I ever see this tool running in android using termux but i don't know how may you ever see too.
I ever see this tool running in android using termux but i don't know how may you ever see too.
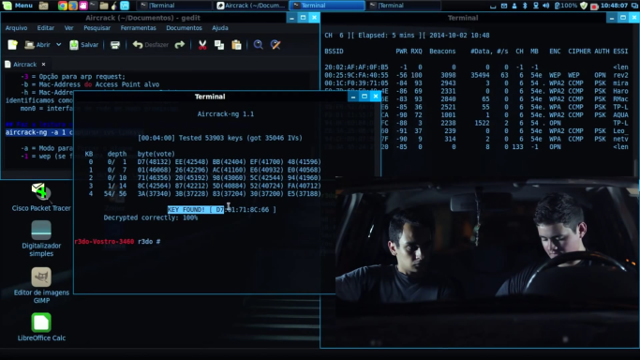
2. Aircrack-ng
Aircrack-ng is one of the best wireless penetration tools for WEP/WAP/WPA2 crackers used worldwide!
It works by taking packets from the network, and analyzing them through retrieved passwords. It also has a console interface. In addition, the Aircrack-ng also uses standard FMS (Fluhrer, Mantin and Shamir) attacks, along with improvements like the Korek and PTW attacks to accelerate the attack, faster than WEP.
If you find it difficult to use Aircrack-ng, just check out the online tutorials.
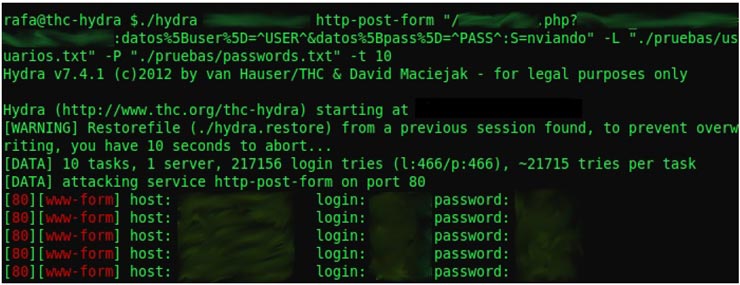
3. THC Hydra
THC Hydra uses brute force attack to automatically decrypt any remote authentication service. Supports fast dictionary attacks for more than 50 protocols, including FTP, https, telnet, etc.
You can use it to break web scanners, wireless networks, package builders, gmail, and so on.
Hidra - Login Cracker
4. WireShark
WireShark is an open source parser that you can use for free. However, you can see activities in the network from the microscopic level as well as access to pcap files, customizable reports, advanced triggers, alerts, etc.
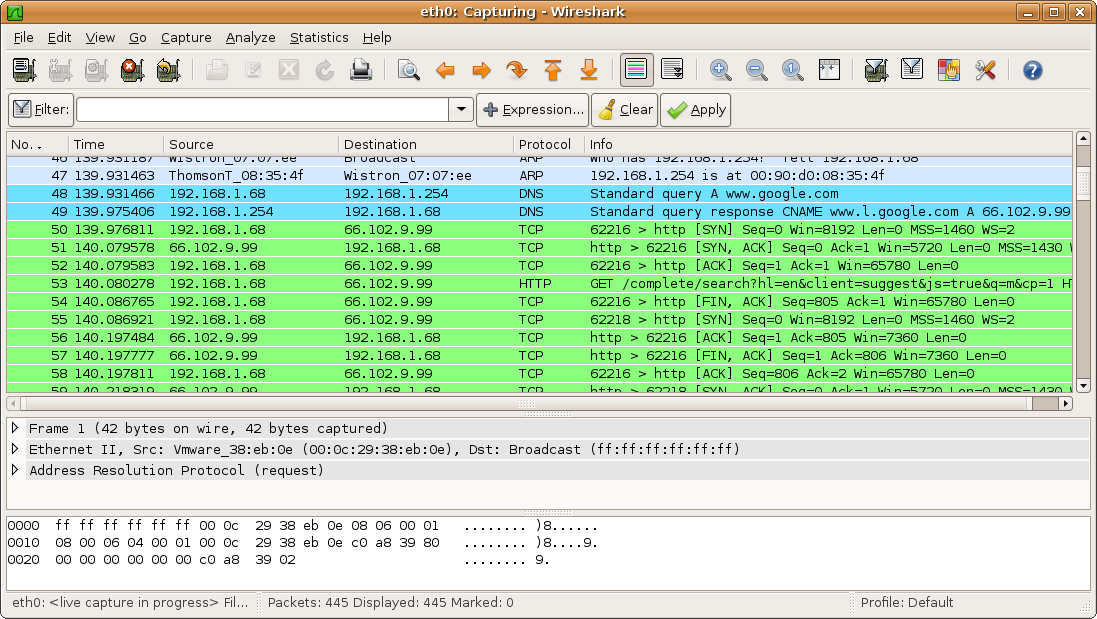 |
| Credit : Wikipedia |
It is said to be the world's most widely used network protocol analyzer for Linux.
5. John the Ripper
John the Ripper is another common tool used in the hacking community (and hacking). Initially developed for Unix systems, it is now available in more than 10 OS distributions.
It has a customizable cracker, automatic password fragmentation, brute force attack and dictionary attack (among other cracking modes).
 |
| Credit: Wikimedia |
John The Ripper Password Cracker
6. NetCat
Netcat, usually abbreviated as nc, is a network utility through which you can use TCP / IP protocols to read and write data to network connections.
 |
| Credit : Wikimedia |
You can use it to create any kind of connection, as well as to troubleshoot and debug networks using tunnel mode, port scanning, etc.
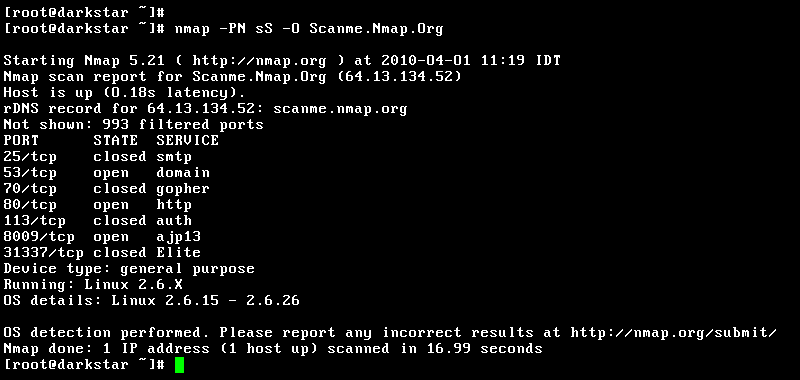
7. Nmap
Nmap (Network Mapper) is a free and open source utility that system administrators use to discover networks and review their security.
It runs fast, well documented, contains graphical user interface, supports data transfer, network inventory, ect.
Discover Nmap Networks and Security Checking Tool
8. Nikto2
Nikto2 is a free and open source web scanner for fast and comprehensive web page testing. To do this, it looks for more than 6,500 potentially dangerous files, versions of legacy software, vulnerable server configurations, and server-specific issues.
 |
| Credit : Wikimedia |
9. Maltego
Maltego is a monopolistic program, but it is widely used for open-source criminal research and search and intelligence. It is a utility to analyze GUI links that provide real-time data mining, as well as image information sets that use node-based graphics and multiple-order connections.
10. Snort
Snort is a free and open source NIDS that can detect security holes on your computer.
With it you can run traffic analysis, search / compare content, record packets in IP networks and detect a variety of network attacks, among other features, all in real time.
11. Yersinia
Yersinia, named for yersinia bacteria, is a network utility designed to exploit weak network protocols by simulating being a testing and analysis framework for secure network systems.
Provides attacks for IEEE 802.1Q, Fast Standby Routing Protocol (HSRP), Cisco Discovery Protocol (CDP), etc.
12. BeEF (Browser Framework)
BeEF, as the name suggests, is a breakthrough tool that focuses on browser vulnerabilities. However, you can evaluate the security of the target environment by using attack vectors from the side
13. Nessus Vulnerability Scanner
Nessus is a remote wipe tool that you can use to check your computers for security holes. This software does not effectively block the security holes in your computers, but you can detect them by running more than 1,200 vulnerability checks and trigger alerts if necessary to perform any security patch.
 |
| Credit : Wikimedia |
Nessus Scanner Vulnerability
14. Kismet Wireless
Kismet Wireless is an intrusion detection system, a network detector, and a password detector. Works mostly with Wi-Fi (IEEE 802.11) networks and can have extended functionality using plug-ins.
 |
| Credit: Wikimedia |
15. Hashcat
Hashcat is known in the security experts community among the fastest and oldest tool to restore and restore the password in the world. It is open source and has a kernel engine in the kernel, more than 200 fragmentation types, a built-in reference system, etc.
16. Burp Suite Scanner
Burp Suite Scanner is an integrated professional GUI testing platform for testing security vulnerabilities for web applications.
Kali Linux and Ubuntu - Which Distro is better to hack?
It combines all test and penetration tools into a community version (free) and in a professional edition ($ 349 per user / year).
Security vulnerability burping scanner
17.Pixiewps
Pixiewps is an offline utility that relies on brute force to exploit software applications with little or no entropy. It was developed by Dominique Bonjard in 2004 to use "futile attack" to educate students.
Depending on the strength of the passwords you are trying to decrypt, Pixiewps can do the task in seconds or minutes.
18. Wifite2
Wifite2 is a free, open source, open-source Python wireless utility designed to work perfectly with pen test distributions. It's a complete rewrite of Wifite, so it offers improved performance.
Do a good job of hiding and decrypting hidden decrypts, decrypting weak WEP passwords using a list of decryption techniques, etc.
19. GNU Mac Changer
GNU MAC Changer is a network utility that makes it easier and faster to handle MAC addresses for network interfaces.
GNU Mac Changer
20. Fern Wifi Cracker
Fern Wifi Cracker is a Python-based wireless security tool to review network vulnerabilities. With it, you can break and restore WEP/WPA/WPS keys, as well as many network-based attacks on Ethernet-based networks.
 |
| Credit: Wikimedia |
Clonclussion
Well, ladies and gentlemen, we've come to the end of our long list of penetration tests and hacking tools for Kali Linux.
All applications listed are current and still used today. If we lose your address, feel free to let us know in the comments section below.
Source and image from Fossmint, Wikipedia
Regards: Linuxergeeks, Miripgeeks.
- [message]
- ##laptop## Support
- Support Us by Disable your ad block.
- thank you



















COMMENTS